Difference between revisions of "Attack carriers"
(Created page with "Overview of channels to deploy a (malicious) print job Various channels like USB, LPD, IPP, SMB, or raw port 9100 p...") |
|||
| Line 58: | Line 58: | ||
|} | |} | ||
| − | It must be noted these | + | It must be noted that these are not the only possible attack scenarios. For example using social engineering to make a victim print a malicious document is not even covered in this wiki yet – neither are new methods to deploy (potentially malicious) print jobs like cloud-based printing. |
== Attacker Models == | == Attacker Models == | ||
| Line 64: | Line 64: | ||
A '''physical attacker''' has the capability to print documents from USB stick or via USB/parallel cable. An (wired or wireless) attacker connecting through a '''TCP/IP network''' can deploy print jobs over LPD, IPP, port 9100/tcp, FTP, SMB and the embedded web server. Under the assumption that no strong user authentication like smart card based access control or SSL client certificates is enforced, both attacker models do obviously have a channel to print which is the precondition for further attacks to be carried out. Both are certainly quite strong attacker models because they require direct access – either physical or logical – to the device. However, in penetration testing scenarios where sneaking into the building is not an option and the printer is not directly reachable over the internet, other deployment channels are required. In such cases, the '''victim's web browser''' can be used as a carrier for printer malware as discussed in [[cross-site printing]]. | A '''physical attacker''' has the capability to print documents from USB stick or via USB/parallel cable. An (wired or wireless) attacker connecting through a '''TCP/IP network''' can deploy print jobs over LPD, IPP, port 9100/tcp, FTP, SMB and the embedded web server. Under the assumption that no strong user authentication like smart card based access control or SSL client certificates is enforced, both attacker models do obviously have a channel to print which is the precondition for further attacks to be carried out. Both are certainly quite strong attacker models because they require direct access – either physical or logical – to the device. However, in penetration testing scenarios where sneaking into the building is not an option and the printer is not directly reachable over the internet, other deployment channels are required. In such cases, the '''victim's web browser''' can be used as a carrier for printer malware as discussed in [[cross-site printing]]. | ||
| − | → ''Related | + | → ''Related articles:'' [[USB drive or cable]], [[Port 9100 printing]], [[Cross-site printing]] |
Revision as of 10:00, 31 January 2017
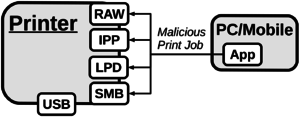
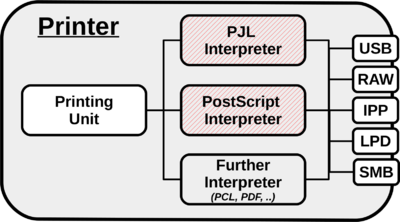
Various channels like USB, LPD, IPP, SMB, or raw port 9100 printing can be used as carriers to deploy malicious print jobs. While it is possible the attack printing protocols themselves, most attacks discussed in this wiki are targeted for the PostScript and PJL interpreters. The payload is just routed by any of the printing channels. This is important to note because it means whenever the attacker can somehow ‘print’ she can attack and exploit those interpreters.
This fact makes it very harder for the blue team (network administrators, for example) to defend against printer attacks. Many devices even allow printing (and therefore exploitation) by uploading a raw file to the printer's FTP service or to a form on the embedded web server. To get an impression, an overview of printing channels supported by various printer models is given below.
| Printer model | LPD | IPP | Raw | Web | FTP | SMB | USB |
|---|---|---|---|---|---|---|---|
| HP LaserJet 1200 | ✔ | ✔ | |||||
| HP LaserJet 4200N | ✔ | ✔ | ✔ | ✔ | |||
| HP LaserJet 4250N | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| HP LaserJet P2015dn | ✔ | ✔ | ✔ | ✔ | |||
| HP LaserJet M2727nfs | ✔ | ✔ | ✔ | ✔ | |||
| HP LaserJet 3392 AiO | ✔ | ✔ | ✔ | ✔ | |||
| HP Color LaserJet CP1515n | ✔ | ✔ | ✔ | ||||
| Brother MFC-9120CN | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Brother DCP-9045CDN | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Lexmark X264dn | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Lexmark E360dn | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Lexmark C736dn | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Dell 5130cdn | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Dell 1720n | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Dell 3110cn | ✔ | ✔ | ✔ | ✔ | |||
| Kyocera FS-C5200DN | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Samsung CLX-3305W | ✔ | ✔ | ✔ | ✔ | |||
| Samsung MultiPress 6345N | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| Konica bizhub 20p | ✔ | ✔ | ✔ | ✔ | ✔ | ||
| OKI MC342dn | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Konica bizhub C454e | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
It must be noted that these are not the only possible attack scenarios. For example using social engineering to make a victim print a malicious document is not even covered in this wiki yet – neither are new methods to deploy (potentially malicious) print jobs like cloud-based printing.
Attacker Models
A physical attacker has the capability to print documents from USB stick or via USB/parallel cable. An (wired or wireless) attacker connecting through a TCP/IP network can deploy print jobs over LPD, IPP, port 9100/tcp, FTP, SMB and the embedded web server. Under the assumption that no strong user authentication like smart card based access control or SSL client certificates is enforced, both attacker models do obviously have a channel to print which is the precondition for further attacks to be carried out. Both are certainly quite strong attacker models because they require direct access – either physical or logical – to the device. However, in penetration testing scenarios where sneaking into the building is not an option and the printer is not directly reachable over the internet, other deployment channels are required. In such cases, the victim's web browser can be used as a carrier for printer malware as discussed in cross-site printing.
→ Related articles: USB drive or cable, Port 9100 printing, Cross-site printing